Shell In A Box is AJAX terminal implementation provided by CentOS and Ubuntu. The plugin provides access to Shell In A Box from DirectAdmin UI. Additionally users can whitelist their IPs along with SIAB (and optionally SSH) port in CSF firewall. The ports can thus be left blocked by default.
As prerequsites you should have CSF/LFD firewall with LF_IPSET enabled. ipset binary should also be present.
CentOS 7 and 8
yum install shellinabox ipset
sed -i -r 's|^(OPTS=").*|\1 -m '*' --no-beep --disable-ssl-menu --verbose -s /:SSH:localhost:22 -n --user-css Normal:+white-on-black.css,Reverse:-white-on-black.css"|' /etc/sysconfig/shellinaboxd
systemctl enable --now shellinaboxdEnsure SSH port in above command matches yours. Use of proxy is optional and described in Ubuntu section.
CentOS 8 (Rocky Linux 8, AlmaLinux 8) users may miss shellinabox RPM. It can be easily built with:
yum -y install gcc wget make rpm-build autoconf automake libtool openssl-devel zlib-devel
wget https://download-ib01.fedoraproject.org/pub/epel/7/SRPMS/Packages/s/shellinabox-2.20-5.el7.src.rpm
rpmbuild --rebuild shellinabox-2.20-5.el7.src.rpm
rpm -Uvh /root/rpmbuild/RPMS/x86_64/shellinabox-2.20-5.el8.x86_64.rpmUbuntu 18.04
apt install shellinabox ipset
sed -i -r 's|^(SHELLINABOX_ARGS=").*|\1--no-beep --disable-ssl-menu -s /:SSH:localhost:1033 -n --localhost-only -t"|' /etc/default/shellinaboxTo get white on black terminal:
cd /etc/shellinabox/options-enabled
rm -f "00+Black on White.css" "01_Monochrome.css"
mv "00_White On Black.css" "00+White On Black.css"Enable and start SIAB:
systemctl enable --now shellinaboxDue to problems with TLS 1.3 we need to use proxy and bind SIAB to 127.0.0.1. This keeps connections secured between client and server using HTTPS and http proxying on loopback is still secured with SSH. You can use it also with Centos 7 (that works fine with TLS 1.3) if you wish.
mkdir -p /usr/local/directadmin/custombuild/custom/ap2/conf/extra
cp /etc/httpd/conf/extra/httpd-includes.conf /usr/local/directadmin/custombuild/custom/ap2/conf/extra
PUBLIC_IP=`hostname -I |awk '{print $1}'`
cat >>/usr/local/directadmin/custombuild/custom/ap2/conf/extra/httpd-includes.conf<<EOF
Listen $PUBLIC_IP:4200
<VirtualHost $PUBLIC_IP:4200>
ServerName $HOSTNAME
SSLEngine on
SSLCertificateFile /etc/httpd/conf/ssl.crt/server.crt
SSLCertificateKeyFile /etc/httpd/conf/ssl.key/server.key
SSLCACertificateFile /etc/httpd/conf/ssl.crt/server.ca
<IfModule mod_proxy.c>
ProxyPreserveHost On
ProxyPass / http://127.0.0.1:4200/
ProxyPassReverse / http://127.0.0.1:4200/
</IfModule>
</VirtualHost>
EOF
/usr/local/directadmin/custombuild/build rewrite_confsPlugin installation
You will receive plugin download URL in your license email. Now you can install the plugin and see ‘check’ results like below.
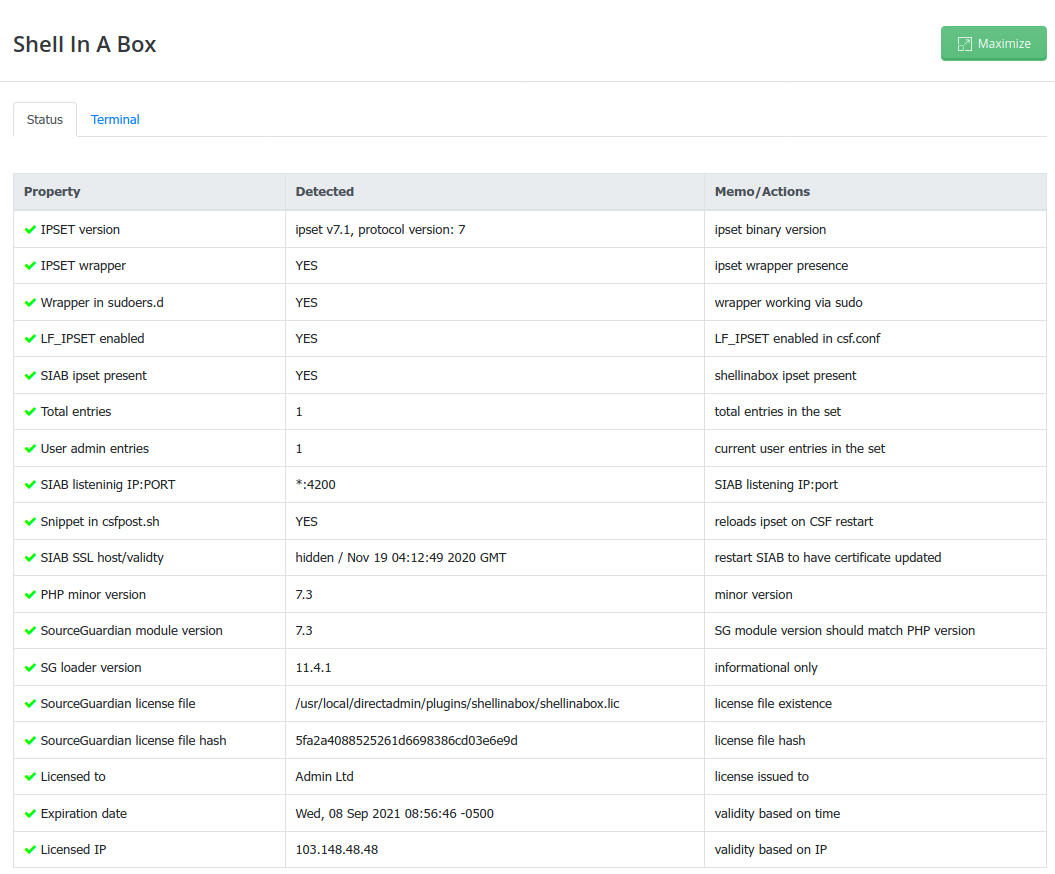
Plugin demo
Notes
- CSF will block IPs with multiple failures like it normally does with SSH.
- Ensure
PasswordAuthentication yesexists in/etc/ssh/sshd_config. You may add the 2 lines at the bottom to ensure admin and root can only login with key.
Match User root,admin
PasswordAuthentication no- We tested it in a configuration where all communication goes thru DirectAdmin (like any typical plugin) using PHP/curl as proxy and found it causes delay by spawning PHP for each AJAX request (say keypress) and thus gets a bit slow (although this would provide another layer of security forcing additional user authentication by DirectAdmin). Direct access from browser to port 4200 provides normal typing experience and so we went this way. You still need to login like you would do with Putty or other client as SIAB works as SSH proxy.
- Connections to SIAB port (and optionally SSH port) are limited with user manageable IP whitelist (CSF ipset).
- If you get double keypress echo then please reload the page with Ctrl+F5 or similar shortcut.
- On Ubuntu 18.04 you can get
command-line line 0: Unsupported option "rhostsrsaauthentication"
command-line line 0: Unsupported option "rsaauthentication"This is a non-harmful bug that can be corrected by rebuilding SIAB from source.
SSL for SIAB is updated on SIAB restart (DA hostname SSL is used).
- Files added/modified by installer outside plugin directory:
- /etc/sudoers.d/shellinabox
- /etc/csf/csfpost.sh
- /usr/local/bin/ipset_shellinabox_wrapper.sh
- /etc/systemd/system/shellinaboxd.service.d/override.conf
- If you get CSS missing for the plugin in Directadmin, please ensure you are accessing SIAB plugin with server’s hostname and https in URL as shellinabox daemon is using SSL certificate for hostname and CORS mismatch can happen.